A brand new quantum countdown web site initiatives a two– to three-year window for quantum computer systems to interrupt broadly used public key cryptography, putting Bitcoin inside its scope.
Websites like The Quantum Doom Clock, operated by Postquant Labs and Hadamard Gate Inc., bundle aggressive assumptions about qubit scaling and error charges right into a timeline that spans the late 2020s to early 2030s for a cryptographically related quantum laptop.
This framing doubles as product advertising and marketing for post-quantum tooling, however that you must learn the wonderful print to note that disclosure.
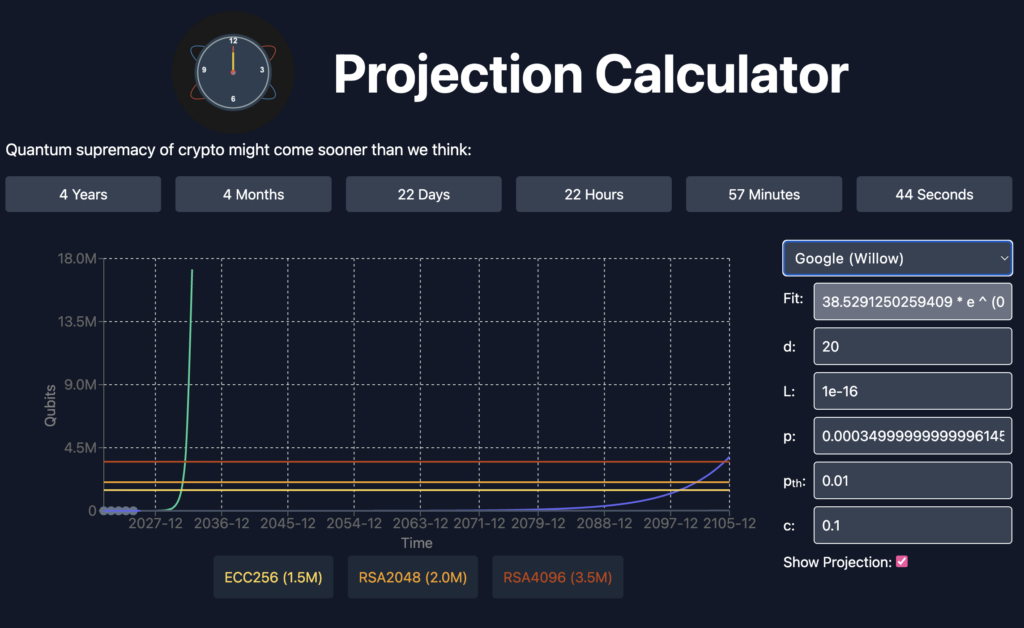
Based on the Quantum Doom Clock, latest useful resource estimates that compress logical-qubit counts, mixed with optimistic {hardware} error developments, counsel that the required physical-qubit class for breaking ECC falls into the few-million vary underneath favorable fashions.
The clock’s presets depend on exponential {hardware} development and bettering constancy with scale, whereas runtime and error-correction overheads are handled as surmountable on a brief fuse.
Authorities requirements our bodies will not be treating a 2027 to 2031 break as a base case.
The U.S. Nationwide Safety Company’s CNSA 2.0 steering recommends that Nationwide Safety Programs ought to full their transition to post-quantum algorithms by 2035, with staged milestones earlier than then, a cadence echoed by the UK Nationwide Cyber Safety Centre.
This requires figuring out quantum-sensitive providers by 2028, prioritizing high-priority migrations by 2031, and finishing them by 2035.
The coverage horizon serves as a sensible danger compass for establishments that should plan capital budgets, vendor dependencies, and compliance applications, implying a multi-year migration arc relatively than a two-year cliff.
Laboratory progress is actual and related, but it doesn’t exhibit the mixture of scale, coherence, logical gate high quality, and T-gate manufacturing facility throughput that Shor’s algorithm would require at Bitcoin-breaking parameters.
Based on Caltech, a neutral-atom array with 6,100 qubits has reached 12.6-second coherence with high-fidelity transport, an engineering step towards fault tolerance relatively than an indication of low-error logical gates at correct code distances.
Google’s Willow chip work highlights algorithmic and {hardware} advances on 105 qubits, claiming exponential error suppression with scale on particular duties. In the meantime, IBM has demonstrated a real-time error-correction management loop working on commodity AMD {hardware}, which is a step towards programs plumbing fault tolerance.
None of those set items removes the dominant overheads that prior useful resource research recognized for classical targets like RSA and ECC underneath floor code assumptions.
A broadly cited 2021 evaluation by Gidney and Ekerå estimated that factoring RSA-2048 in about eight hours would wish roughly 20 million noisy bodily qubits at round 10⁻³ bodily error charges, underscoring how distillation factories and code distance drive totals greater than uncooked system counts.
For Bitcoin, the earliest materials vector is essential publicity on-chain relatively than harvest-now-decrypt-later assaults towards SHA-256. Based on Bitcoin Optech, outputs that already reveal public keys, equivalent to legacy P2PK, reused P2PKH after spend, and a few Taproot paths, would turn out to be targets as soon as a cryptographically related machine exists.
On the similar time, typical P2PKH stays protected by hashing till it’s spent. Core contributors and researchers monitor a number of containment and improve paths, together with Lamport or Winternitz one-time signatures, P2QRH handle codecs, and proposals to quarantine or drive rotation of insecure UTXOs.
Proponents behind BIP-360 declare that greater than 6 million BTC are held in quantum-exposed outputs throughout P2PK, reused SegWit, and Taproot, which is greatest understood as an higher certain from advocates relatively than a consensus metric.
The economics of migration matter as a lot because the physics.
With NIST now finalizing FIPS-203 for key encapsulation and FIPS-204 for signatures, wallets and exchanges can implement the chosen household right this moment.
Based on NIST FIPS-204, ML-DSA-44 has a 1,312-byte public key and a 2,420-byte signature, that are orders of magnitude bigger than these of secp256k1.
Underneath present block constraints, changing a typical P2WPKH enter witness with a post-quantum signature and public key would improve the per-input dimension from tens of digital bytes to a number of kilobytes. This might compress throughput and push charges greater until paired with aggregation, batch-verification-friendly constructs, or commit-reveal patterns that transfer bulk knowledge off scorching paths.
Establishments with many exposed-pubkey UTXOs have an financial incentive to de-expose and rotate methodically earlier than a scramble concentrates demand right into a single payment spike window.
The divergences between a marketing-aggressive clock and institutional roadmaps might be summarized as a set of enter assumptions.
Latest papers that cut back logical-qubit counts for factoring and discrete log issues could make a few-million bodily qubit goal seem nearer, however solely underneath assumed bodily error charges and code distances that stay past what labs show at scale.
The mainstream lab view displays stepwise system scaling the place including qubits can erode high quality, with a path towards 10⁻⁴ to 10⁻⁵ error charges as code distance grows.
A conservative learn locations materials limits, management complexity, and T-factory throughput as fee limiters that reach timelines into the 2040s and past, absent breakthroughs.
The coverage drumbeat to finish migrations by 2035 aligns extra with the stepwise and conservative instances than with exponential {hardware} trajectories.
*Totals depend upon floor code distance, logical gate error targets, and T-gate distillation throughput. See Gidney and Ekerå (2021).
Ahead-looking markers to look at are concrete.
- Peer-reviewed demonstrations of long-lived logical gates, not solely reminiscence, at code distance round 25 with sub-10⁻⁶ logical error charges.
- Sensible T-gate distillation factories that ship throughput for algorithms with 10⁶-plus logical qubits.
- Bitcoin Enchancment Proposals that advance post-quantum signature pathways from prototype to deployable customary, together with codecs that maintain bulk artifacts off the recent path.
- Public commitments by main exchanges and custodians to rotate uncovered outputs, which might distribute payment stress throughout time.
The Doom Clock’s utility is narrative, compressing uncertainty into urgency that funnels to a vendor resolution.
The danger compass that issues for engineering and capital planning is anchored by NIST requirements now finalized, authorities migration deadlines round 2035, and the lab milestones that may mark actual inflection factors for fault tolerance.
Based on NIST’s FIPS-203 and FIPS-204, the tooling path is offered right this moment, which implies wallets and providers can begin de-exposing keys and testing bigger signatures with out accepting a two-year doomsday premise.
Bitcoin’s hash-then-reveal design decisions already delay publicity till spending time on frequent paths, and the community’s playbook consists of a number of rotation and containment choices when credible alerts, not vendor clocks, point out it’s time to proceed.
It’s, nevertheless, price remembering that when quantum computer systems make Bitcoin’s cryptography susceptible, different legacy programs are additionally uncovered. Banks, social media, finance apps, and far more may have backdoors left extensive open.
Societal collapse is an even bigger danger than shedding some crypto if legacy programs will not be up to date.
For many who argue that Bitcoin upgrades will probably be slower than these of banks, and many others., keep in mind this, some ATMs and different banking infrastructure around the globe nonetheless run on Home windows XP.